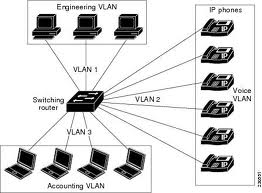
VLANs logically divide a switch into multiple broadcast domains at Layer 2.
Each VLAN can represent a logical grouping of users by function or department. As users in these VLANs move, we simply need to change the VLAN assigned to their switch port. VLANs also enhance security because users in one VLAN cannot communicate to users in another VLAN without the use of a Layer 3 device providing inter-VLAN routing.
VLAN Configuration
VLANs can be statically assigned to switch access ports or dynamically assigned by using a VMPS. By default, all interfaces are assigned to the management VLAN, VLAN 1.
To configure a VLAN:
- Create the VLAN in global configuration:
Switch(config)#vlan2 Switch(config-vlan)#
- The VLAN must be named:
Switch(config-vlan)#vlan2 name ExamPrep
- The desired ports must be added to the new VLAN:
Switch(config)#interfaceFastEthernet 0/1 Switch(config-if)#switchportaccess vlan 2
Voice VLANs
Voice VLANs are used to separate VoIP traffic from data on an access port for QoS, manageability, and traffic confinement.
Switch(config-if)#switchportvoice vlan 30
Trunks
VLANS can span multiple switches using trunks. Trunks multiplex traffic from all VLANs over a single connection. The VLAN identifier is tagged over the trunk using one of the following tagging methods:
- ISL: A Cisco-proprietary trunk that encapsulates the original Ethernet frame with a 26-byte header and a 4-byte CRC.
- IEEE 802.1q: Standards-based VLAN tagging that inserts a 4-byte tag in the original Ethernet frame. Traffic originating from the native VLAN (VLAN 1 by default) is not tagged over the trunk. If native VLAN configuration does not match on both sides, this could cause VLAN leakage.
Trunk Configuration
Switch(config)#interfaceFastEthernet 0/24
Switch(config-if)#switchporttrunk encapsulation [isl|dot1q] Switch(config-if)#switchportmode trunk
Trunks can be secured by allowing only specific VLANs to traverse to switches that specificallyrequire access to those VLANs. The command to specify the VLANs to be included in the “allowed list of VLANs” is switchport trunk allowed vlan {add | remove | except} vlan_list.
VLAN Trunking Protocol
Cisco created VTP to minimize the amount of VLAN administration in switches by enabling a VTP server to multicast VTP advertisements to other switches in the same VTP domain. Switches receiving these advertisements synchronize their VLAN database with the VLAN information advertised from the server, assuming that the revision number is higher.
VTP Modes
Mode Function
Server Default VTP mode that enables you to create, modify, and delete VLANS. These VLANs are advertised to other switches and saved in the VLAN database.
Client Cannot create, modify, or delete VLANs. Forwards advertisements received from the server, but does not save the VLAN configuration in the VLAN database.
Transparent Creates, modifies, and deletes VLANs only on the local switch. Does not participate in VTP but forwards VTP advertisements received from servers. Also saves the VLAN configuration in the VLAN database.
VTP Configuration
Changing the VTP domain name from NULL to ExamPrep:
Switch(config)#vtpdomain ExamPrep
Setting the device VLAN database password to examcram:
Switch(config)#vtppassword examcram
Setting the device to VTP TRANSPARENT mode:
Switch(config)#vtptransparent
InterVLAN Routing
InterVLAN routing requires a Layer 3 device such as router or a Layer 3 switch:
. Router-on-a-stick: The connection between router and switch must be at least Fast
Ethernet speeds and must be a trunk. The router interface consists of subinterfaces to assign an IP gateway for each VLAN. The VLAN is associated with a subinterface using the encapsulation command:
Router(config)#interfaceFastEthernet 0/1 .2
Router(config-subif)#ipaddress 192.168.2.1 255.255.255.0 Router(config-subif)#encapsulationdot1q 2
Router(config)#interfaceFastEthernet 0/1 .3
Router(config-subif)#ipaddress 192.168.3.1 255.255.255.0 Router(config-subif)#encapsulationdot1q 3
. Switched virtual interfaces: VLAN interfaces configured in a Layer 3 switch that enables inter-VLAN routing using ASIC technology:
Router(config)#interfaceVlan 2
Router(config-if)#ipaddress 192.168.2.1 255.255.255.0 Router(config)#interfaceVlan 3
Router(config-if)#ip address 192.168.3.1 255.255.255.0
Port Security
Here’s the configuration that limits the number of MAC addresses that can be dynamically learned on a switch port:
Switch(config-if)#switchportmode access
Switch(config-if)#switchportport-security
Switch(config-if)#switchportport-security maximum 1
Switch(config-if)#switchportport-security violation {protect | restrict| shutdown}
If a violation occurs, the default response of a Catalyst switch is to shut down the port. To havethe port increase a violation counter and alert an administrator using SNMP, use therestrictkeyword. The protectkeyword allows only traffic from the secure port and drops packets from other MAC addresses until the number of MAC addresses drops below the maximum.
To secure an interface by statically assigning the permitted MAC address(es) attached to the port, use the switchport port-security mac-address MAC_address command on the interface. Alternatively, you can have the switch learn these addresses up to the maximum byusing sticky-learned addresses with the commandswitchport port-security mac-address sticky.